For many, “Cryptography” is the little green lock icon next to the web address of their favorite websites, and for others, they might recall the TLS vulnerabilities that have hit in recent years. Data is today’s digital gold, and in the quest to steal critical data, hackers are coming up with clever ways of stealing information. With the ever changing attack landscape in mind, Couchbase Server 6.5 adds a new way to easily configure the server cipher suites. In this blog, we’ll go over the basics of ciphers and explain how you can configure Couchbase to use the latest and greatest ciphers.
Basics of TLS Cipher Suites
A cipher suite is basically a complete set of methods (also known as algorithms) needed to secure a network connection through TLS (Transport Layer Security). Each cipher suite has its own distinct notation as shown below –
TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384
Now, let’s break that down-
- TLS indicates that TLS protocol will be used to establish a secure communication. Remember that a protocol simply defines how the algorithms should be used.
- ECDHE indicates that the Elliptic-Curve Diffie-Hellman will be leveraged for key exchange. This is how the keys will be exchanged between client and server for encrypting and decrypting data.
- ECDSA is the algorithm, in this instance the Elliptic-Curve Digital Signature Algorithm, that is used to create a digital signature for authentication.
- AES_256_CBC indicates that AES encryption with 256-bit key size will be leveraged to encrypt the message, and CBC indicates that the mode will be cipher block chaining.
- SHA384 indicates that the hashing algorithm used for message verification (MAC) and in this example is SHA2 with a 384-bit key.
The TLS Handshake Protocol is responsible for the Cipher Suite negotiation between the client and server (see ‘Server Hello’), authentication of the server and optionally the client, and the secret key exchange (see green arrows below).
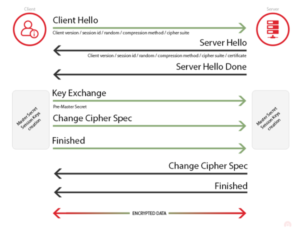
Figure : Client-Server Interaction During TLS Handshake
Setting Cipher Suites in Couchbase 6.5
By default (ie. without explicitly specifying the cipher suites), Couchbase Server picks the strongest common cipher between the client and the server. With Couchbase Server 6.5, you can tell Couchbase which Cipher suites to use.
As shown in the example below, we set the cipher suites in Couchbase to use TLS_RSA_WITH_AES_128_CBC_SHA. This cipher suite is then used across all Couchbase Server services including data, query, index, full-text and analytics.
| # ./couchbase-cli setting-security –cipher-suites TLS_RSA_WITH_AES_128_CBC_SHA -c localhost:8091 -u Administrator -p password –set
SUCCESS: Security settings updated # ./couchbase-cli setting-security -c localhost:8091 -u Administrator -p password –get |
Verifying Cipher Usage
To verify that the cipher is used, we can connect to any of the SSL ports in Couchbase. In the example below, we are connected to port 11207 (the data port over which Couchbase clients connect to the server).
| openssl s_client -connect localhost:11207
CONNECTED(00000003) — Certificate chain 0 s:/CN=127.0.0.1 i:/CN=Couchbase Server de182d2a 1 s:/CN=Couchbase Server de182d2a i:/CN=Couchbase Server de182d2a — Server certificate —–BEGIN CERTIFICATE—– MIIDADCCAeigAwIBAgIIFbB+nPd+hWIwDQYJKoZIhvcNAQELBQAwJDEiMCAGA1UE AxMZQ291Y2hiYXNlIFNlcnZlciBkZTE4MmQyYTAeFw0xMzAxMDEwMDAwMDBaFw00 OTEyMzEyMzU5NTlaMBQxEjAQBgNVBAMTCTEyNy4wLjAuMTCCASIwDQYJKoZIhvcN AQEBBQADggEPADCCAQoCggEBAL7PaNB0n1vxDsg6Z4ydBk7HjlEjzItIGVp6svgF 2A1XW98bIl34D6ZsWHsyj+i9+Xb3saY8HTD8f83QtUkGpve0AQGCHxFE1Dx0Eb2t hMGwSWiL4DAiufa42UGmgJ008D70hpdQS1/ow5wZ1kNmqmHdjzG2wGrdJEGFhwzS lka+HdrDCaQIT6jvtnT3udO0R6yRFxjveEQ5lFX/P4tZeyIWglTT0muRxcxI/7Ln nvUQgoLRta59hxiK1PXQczjP1KPls8OdWnap4HNIbi3WOim9hk/Vn4R6BSvU1N9W Md4WkXw6WgzcPz1khdQTsZzDZbQNV0fI9fcM8nGoh6A1R7sCAwEAAaNGMEQwDgYD VR0PAQH/BAQDAgWgMBMGA1UdJQQMMAoGCCsGAQUFBwMBMAwGA1UdEwEB/wQCMAAw DwYDVR0RBAgwBocEfwAAATANBgkqhkiG9w0BAQsFAAOCAQEACiMJY3512tT+rEFJ 4xe0zGIoJi7ebXz1O8w8a2NBKjwWeZ2oCco0CxILfDn1EPH9NBZsiQS7w9OGz7VO pwSVrt6/jRIAAqnFxSUZpKiZ/avNK5kpfufebxaA4ZQzrW4/lePsBRcRl3ENWJup OsE8hD4Xv/LQHnZxZlbq8gQv8ZiJqsi8bRoEML4A4DgTmgvTYgT0XIp9V65H9zZ/ jJEymoUx9eidAdfVo+l8PlE7YgRsrP9f7y5tDARAAmmAmL2mgUmzxqe49Hp8MPDl ocTLZm1ryT+g1xvL/EuuLOACUecInBnWSmzJep7Vw0jzqR92YWht6rM3NGfwNyzT 3hz7ZA== —–END CERTIFICATE—– subject=/CN=127.0.0.1 issuer=/CN=Couchbase Server de182d2a — No client certificate CA names sent — SSL handshake has read 1881 bytes and written 631 bytes — New, TLSv1/SSLv3, Cipher is AES128-SHA Server public key is 2048 bit Secure Renegotiation IS supported Compression: NONE Expansion: NONE |
Conclusion
With Cipher suites available in Couchbase Server 6.5, you can continually update your Couchbase instance to use the latest and greatest ciphers to stay safe. We hope you enjoyed this blog, and as always, we look forward to your feedback. Do take Couchbase Server for a spin and checkout all the new cool features, you can download Couchbase 6.5.
Resources
Download
Documentation
Couchbase Server 6.5 Release Notes
Couchbase Server 6.5 What’s New
Blogs
Blog: Announcing Couchbase Server 6.5 – What’s New and Improved
Blog: Couchbase brings Distributed Multi-document ACID Transactions to NoSQL