What are PrivateLinks?
PrivateLinks are a networking service that allows for the private connection between a cloud service and your virtual network. This connection is made without exposing your data to the public internet, enhancing security by keeping network traffic within the cloud provider’s network. By utilizing PrivateLinks, you can ensure more secure and reliable access to cloud resources, minimizing the risk of external threats and reducing latency by keeping the traffic internal to the cloud provider’s network.
PrivateLinks facilitate uni-directional communication, enhancing the security of network connections by ensuring that traffic can only flow in a single direction. This design helps in preventing unauthorized access and data exfiltration, further solidifying the security benefits of using PrivateLinks for cloud networking.
Note: XDCR is not compatible with Private Links at the moment.
1. Sign into the AWS Management Console
-
- Log in to your AWS Management Console
- You should land on the following page:

- Log in to your AWS Management Console
2. Create a VPC in AWS
-
- In the search bar, enter VPC:

- You should land on the following page:

- This should open the VPC Dashboard:

- Choose your region in the black App Bar. In this example, we are using: US East (N. Virginia) – us-east-1

- Click on Create VPC. This opens a page with your VPC Settings.
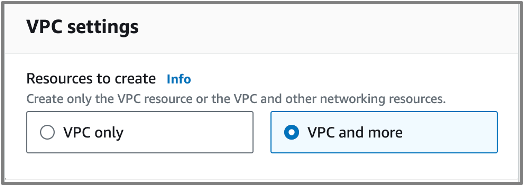
- Resources to create: Select VPC and more.
- Name tag auto-generation: Name your VPC.

Note: Recommendation is to use a meaningful name so you can easily identify which VPC is yours later on in the lab. In this example, we use privatelinkaws but we recommend to use a more personalized name for your testing. - IPV4 CIDR Block: Accept default.

- IPV6 CIDR Block: None.
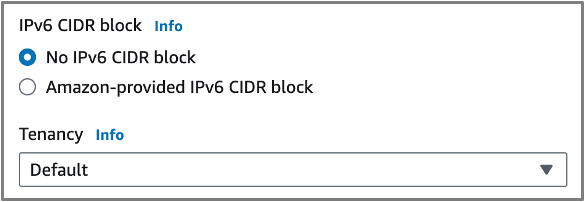
- Tenancy: Default

- Number of AZs: 1

- Number of public subnets: 1

- Number of private subnets: 0
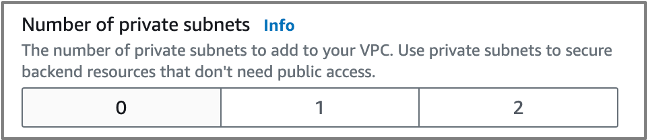
- NAT gateways: 0

- VPC Endpoints: S3 Gateway
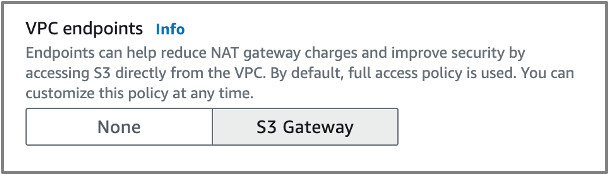
- DNS Options
- Resources to create: Select VPC and more.
- Check the Preview in the right side of the page. Once you’re satisfied, click Create VPC.

- In the search bar, enter VPC:
3. Create AWS EC2 instance
-
- In the search bar, enter EC2.

- You should land into the EC2 Dashboard.
- Make sure that you are in the correct region, like the one where you created your VPC.

- Click Launch Instance.
- This will open a page with your EC2 settings.
- Name: Choose name (eg. Privatelink-tester). Same as before, please choose a more meaningful name.

- Application and OS Image: Amazon Linux

- Instance Type: t2.micro (free)

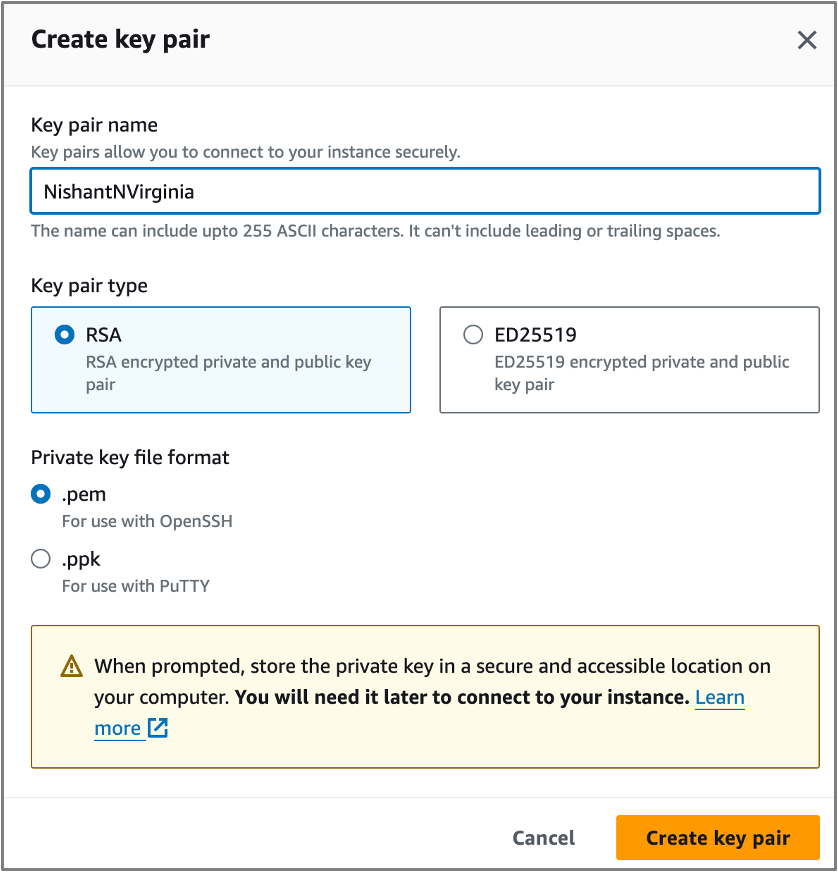
- Key pair login: click on Create a new key pair.
- Network settings
- Click Edit
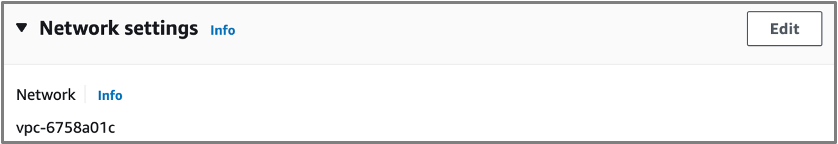
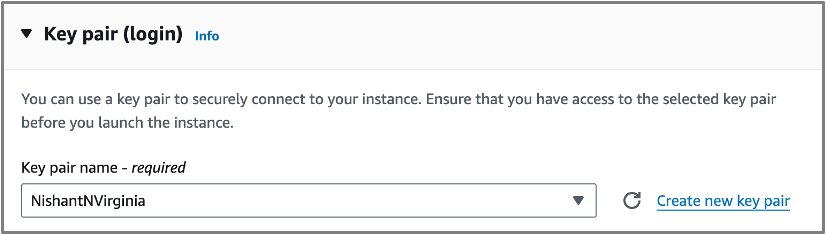
- VPC: choose the same VPC as the one you’ve created previously. You can filter using your VPC name or using the VPC ID.

- Subnet: choose the subnet you created previously. It should be selected automatically as you created only 1 subnet for this VPC.

- Auto-assign public IP: Enable

- Firewall security group: Create Security Group should be selected
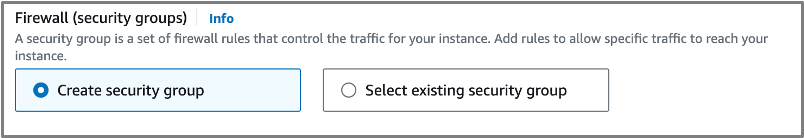
- Inbound security group rules: in the Source type, select MY IP. This will automatically add your IP.
- Click Edit
- Configure Storage: default.

- Application and OS Image: Amazon Linux
- Name: Choose name (eg. Privatelink-tester). Same as before, please choose a more meaningful name.
- Check the summary and click Launch instance.

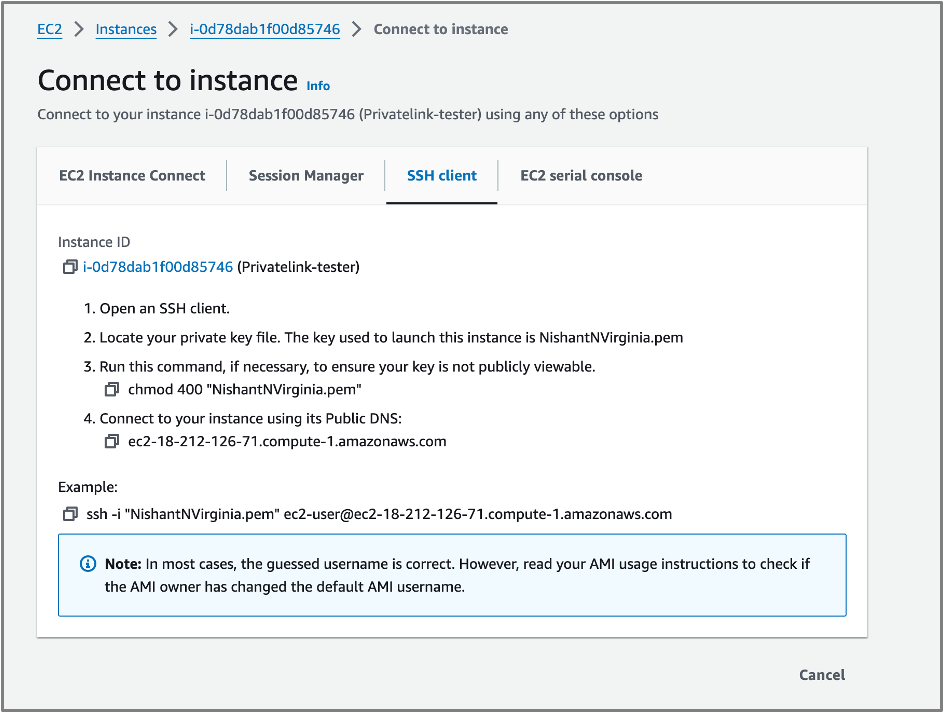
- After a few seconds, you should see that the instance has been successfully launched. Note the EC2 instance ID. In this example: i-0d78dab1f00d85746. Click on the EC2 instance ID.

- In the search bar, enter EC2.
4. Install AWS CLI Tool
-
- To use the AWS CLI Tool, please follow the documentation.
- You should get temporary credentials.
-
- To configure the AWS CLI Tool, simply copy the Option 1, Short-Term Credentials command to set the AWS environment variables and paste it in your terminal. (The below is an example – please paste in your own credentials.)
|
1 2 3 |
$ export AWS_ACCESS_KEY_ID="XXXXXXXXXXXXXXXXXXXXX" $ export AWS_SECRET_ACCESS_KEY="XXXXXXXXXXXXXXXXXXXXXX" $ export AWS_SESSION_TOKEN="XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX” |
5. Create a Capella Database
-
- Login into Capella with your corporate email and credentials.
- Within your project, create a database with the following configuration:
-
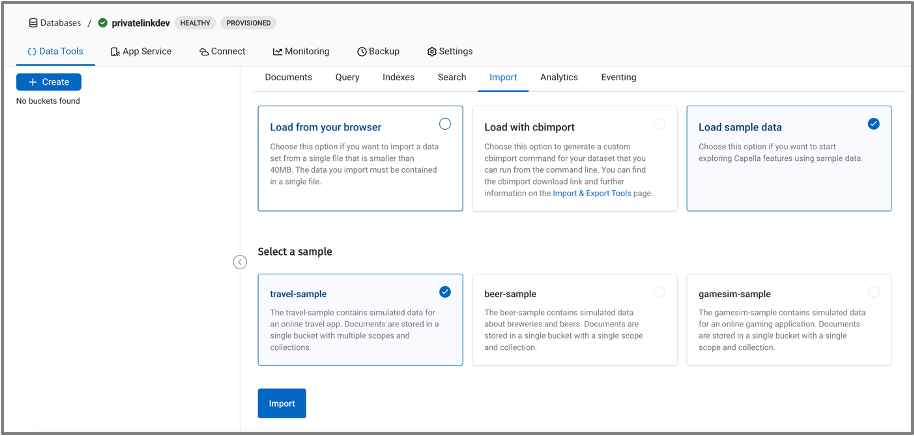
- Once the database is Healthy, deploy travel-sample bucket:
B. Stage 1
In this section, you will learn how to:
|
1. Enable Private Endpoint
-
- In your Capella database, open the Settings page, navigate to Private Endpoint and click Enable Private Endpoint.
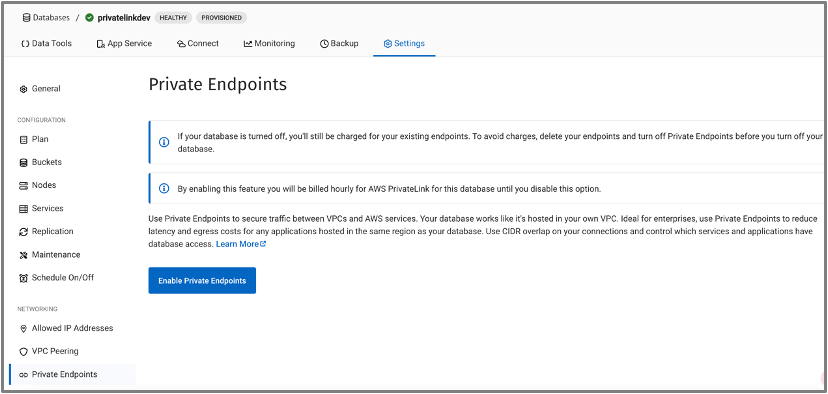
- This action will usually take around 10 minutes to enable Private Endpoint.
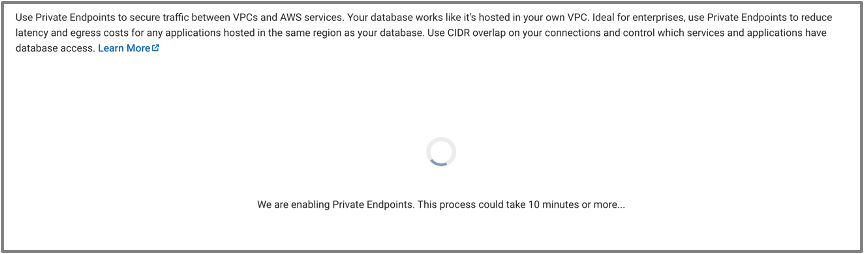
- When ready, you should see that the Private Endpoint DNS is now available in the Capella UI. Also notice that Private Endpoints are billed hourly for AWS Private Endpoints for this database until you disable this option.

- In your Capella database, open the Settings page, navigate to Private Endpoint and click Enable Private Endpoint.
2. Add Private Endpoint
3. Create VPC Endpoint on AWS from CLI
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 |
(base) nishant.bhatia@macbook ~ % aws ec2 create-vpc-endpoint --vpc-id vpc-076a939ba49ce9ab6 --region us-east-1 --service-name com.amazonaws.vpce.us-east-1.vpce-svc-0b4d23fccabd9ea08 --vpc-endpoint-type Interface --subnet-ids subnet-08245a74b701954ca { "VpcEndpoint": { "VpcEndpointId": "<strong>vpce-01dfcbabe2bef175e</strong>", "VpcEndpointType": "Interface", "VpcId": "vpc-076a939ba49ce9ab6", "ServiceName": "com.amazonaws.vpce.us-east-1.vpce-svc-0b4d23fccabd9ea08", "State": "pendingAcceptance", "RouteTableIds": [], "SubnetIds": [ "subnet-08245a74b701954ca" ], "Groups": [ { "GroupId": "sg-0231c72bc71c7753c", "GroupName": "default" } ], "IpAddressType": "ipv4", "DnsOptions": { "DnsRecordIpType": "ipv4" }, "PrivateDnsEnabled": false, "RequesterManaged": false, "NetworkInterfaceIds": [ "eni-0cdc0c23ab3760c13" ], "DnsEntries": [ { "DnsName": "vpce-01dfcbabe1bef165e-vq1r3b0l.vpce-svc-0b5d22fccabd9ea08.us-east-1.vpce.amazonaws.com", "HostedZoneId": "Z7HUB22XULQXV" }, { "DnsName": "vpce-01dfcbabe1aef175e-vq1r3b0l-us-east-1a.vpce-svc-0b5d23fccaad9ea08.us-east-1.vpce.amazonaws.com", "HostedZoneId": "Z7HUB22UULQYV" } ], "CreationTimestamp": "2024-01-04T16:29:47.138Z", "OwnerId": "306776352488" } } |
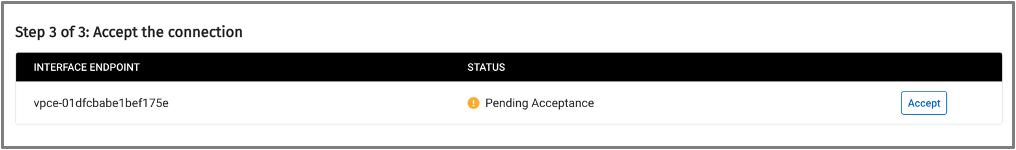
4. Complete Connection
C. Stage 2
In this section, you will learn how to:
|
1. Enable Private DNS on AWS
-
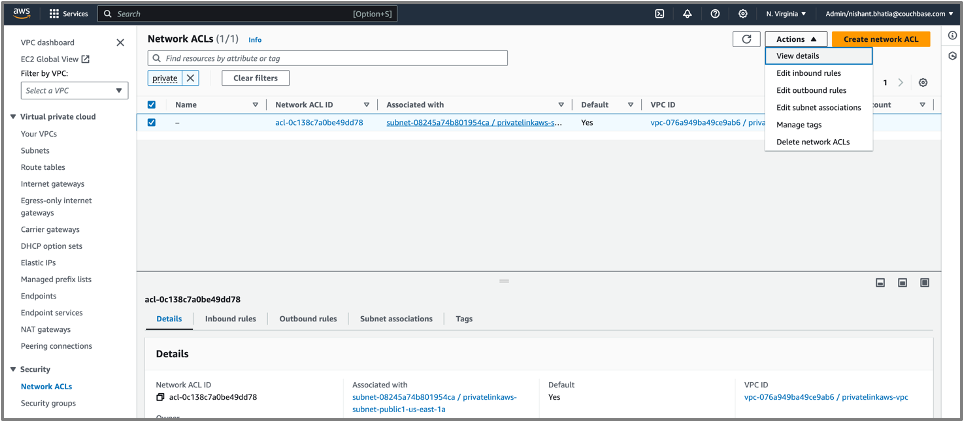
- Navigate to the VPC Dashboard, click Endpoints in the left menu and filter on your VPC Name. You will see at least 2 endpoints:
- The S3 endpoint created by AWS
- An unnamed Endpoint, created by the CLI command

- Open the unnamed Endpoint (in this case vpce-01dfcbabe1bef175e) and from the Actions drop-down, with the same ID as the one provided in the Capella Private Endpoint Interface Endpoint list. Select Modify private DNS name.

- Check Enable for this endpoint and click Save Changes.
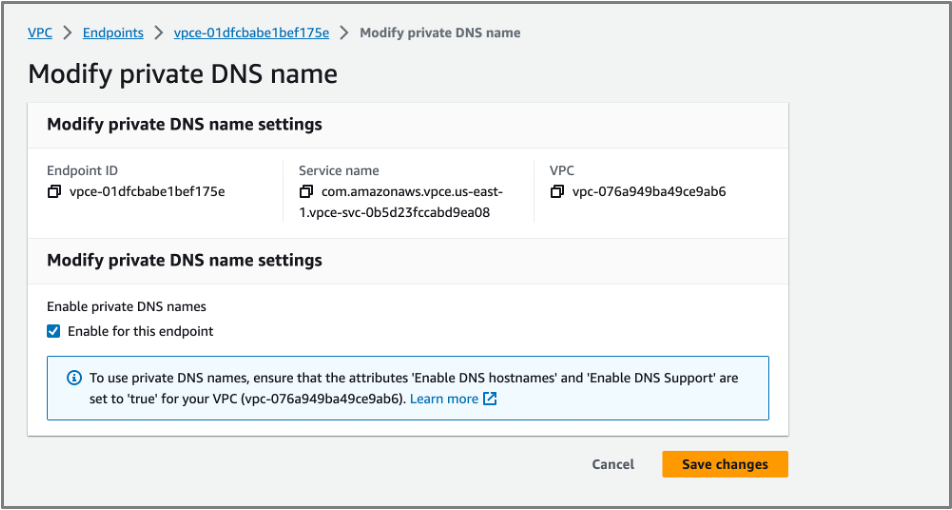
- Navigate to the VPC Dashboard, click Endpoints in the left menu and filter on your VPC Name. You will see at least 2 endpoints:
2. Edit Ingress Rules for Private Endpoint on AWS
-
- Let’s first get the CIDR Block of your VPC.
- Click Your VPCs in the VPC Dashboard
- Filter on your VPC Name.

- In the bottom main panel, note the IPV4 CIDR. It should be 10.0.0.0/16

- Let’s now get the Security Group of Endpoint
- Click on Endpoints in the VPC Dashboard
- Filter on your VPC Name. You will see at least 2:
- Choose the unnamed Endpoint
- At panel bottom navigate to Security Groups Tab
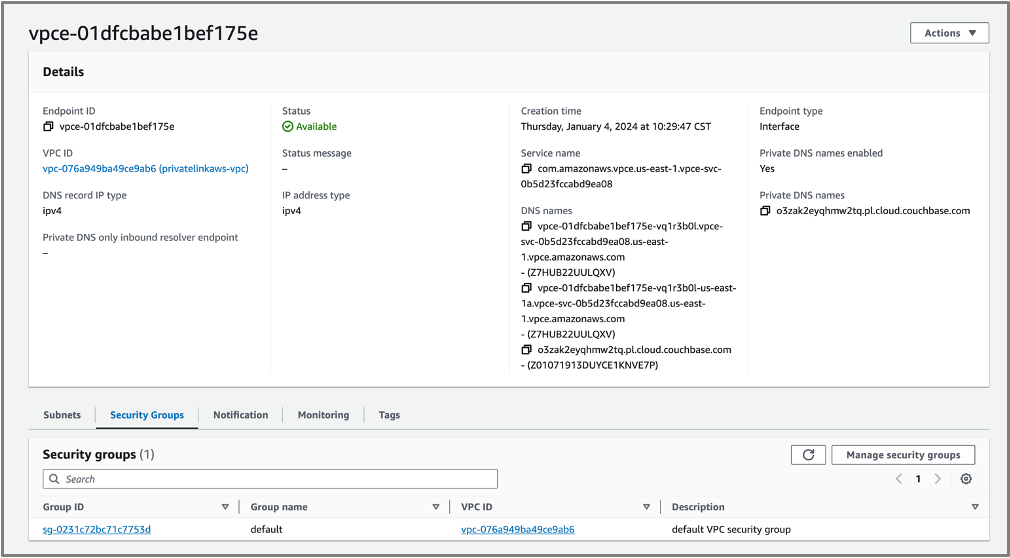
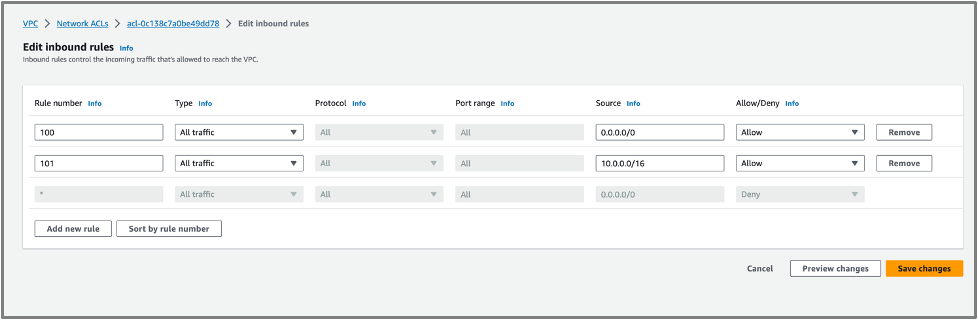
- Click the Group ID Link and locate Inbound Rule. There will be one Inbound Rule which will be chosen by default. Click Edit Inbound rules.

- Click Add Rule
- Let’s first get the CIDR Block of your VPC.
3. Edit Network ACL for Private Endpoint on AWS
D. Test Private Endpoint with an Application
In this section, you will learn how to:
|
1. Add Capella Security Prerequisites
-
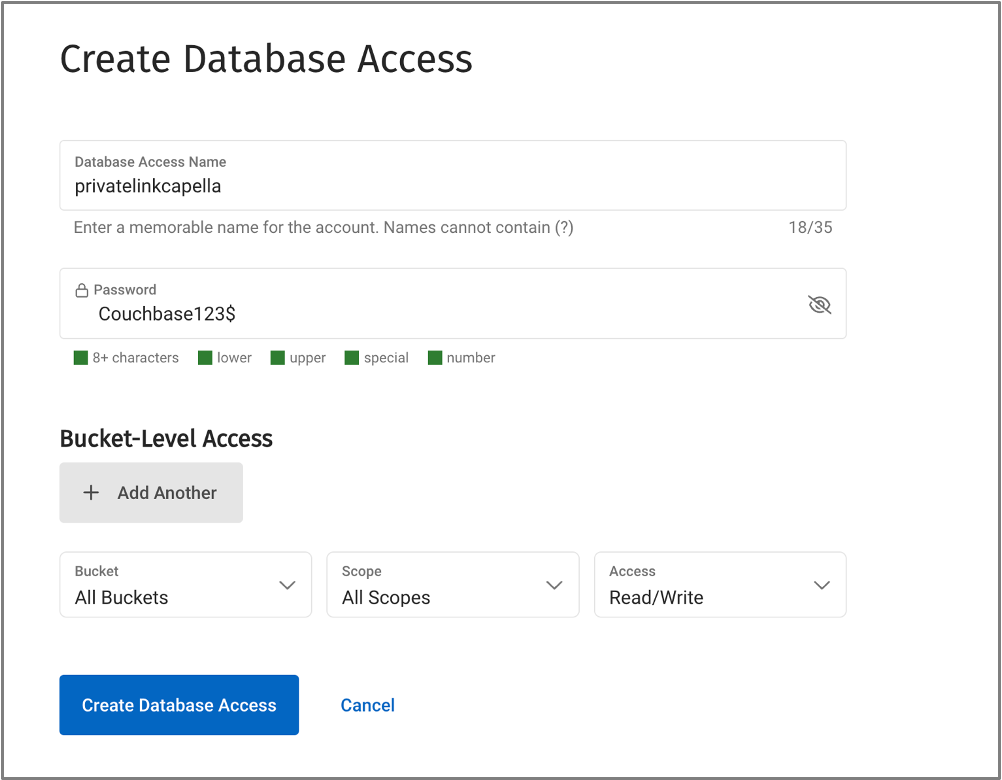
- In your Capella database, create Database Credentials. Example: privatelinkcapella/Couchbase123$
- In Capella, copy the private Endpoint. In this example, this is o3bak2eyqhmw2tq.pl.cloud.couchbase.com

- In the Capella Settings of your database, open the Security Certificate page and download the certificate.
- You should get an privatelinkdev-root-certificate.txt file or similar depending on your database name.

2. Install Python in your AWS EC2 instance
-
- Let’s now SSH into EC2 Instance.
- Let’s now connect to the instance from your laptop.
- Click SSH client Tab and follow the instructions to make sure your private key is accessible from your terminal and not publicly viewable.
- Click SSH client Tab and follow the instructions to make sure your private key is accessible from your terminal and not publicly viewable.
|
1 |
chmod 400 NishantNVirginia.pem |
-
-
- Locate the ssh Example command at the bottom and run it in your terminal.
-
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
$ ssh -i "NishantNVirginia.pem" ec2-user@ec2-18-212-116-71.compute-1.amazonaws.com nishant.bhatia@JGWXHT4VFM downloads % ssh -i "NishantNVirginia.pem" ec2-user@ec2-18-212-126-71.compute-1.amazonaws.com The authenticity of host 'ec2-18-212-126-71.compute-1.amazonaws.com (18.212.126.71)' can't be established. ED25519 key fingerprint is SHA256:RJorms+Tb2vpQxACTE7gcafmFpeP6xQSm3/Ny0WZYJg. This key is not known by any other names Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added 'ec2-18-212-116-71.compute-1.amazonaws.com' (ED25519) to the list of known hosts. , #_ ~\_ ####_ Amazon Linux 2023 ~~ \_#####\ ~~ \####| ~~ \#/ ___ https://aws.amazon.com/linux/amazon-linux-2023 ~~ V~' '-> ~~~ / ~~._. _/ _/ _/ _/m/' |
-
- Let’s now install the Python SDK in the instance. Note: the following installation is composed of 3 commands. Make sure you run each of those commands separately in your terminal. Each command will also interactively ask for confirmation of package installation.
|
1 2 3 4 5 |
sudo yum update sudo yum install gcc gcc-c++ git python3-devel python3-pip openssl-devel sudo yum install openssl-devel sudo yum install openssl python3 -m pip install couchbase |
-
- For the lib, you can also execute the following command.
|
1 2 3 |
sudo yum install openssl11 #it’s okay if this does not execute as the lib are added in openssl-devel |
3. Test a python app connecting to the Capella Private Endpoint
-
- Exit ssh to get back to your local laptop or you can open a new shell window
|
1 |
exit |
-
- Rename the Capella Security .txt certificate you downloaded before as privatelink-cert.pem. Replace the name of the root certificate with your own.
-
-
1mv Downloads/privatelinkdev-root-certificate.txt privatelink-cert.pem
- Let’s copy privatelink-cert.pem into your EC2 instance. In the command below:
- Replace the name of your certificate with your own.
- Replace the Key Pair file with the one you used to create your VPC.
- Replace the ec2 name with your own (reuse the same as the one provided in the SSH Client example).
- Execute the command.
Note that the following scp command is a single command.
-
|
1 2 3 |
cd downloads chmod 400 "NishantNVirginia.pem" scp -i "NishantNVirginia.pem" privatelink-cert.pem ec2-user@ec2-18-212-126-71.compute-1.amazonaws.com:/home/ec2-user |
-
- Copy the following simple python code in your preferred IDE.
- Replace the private endpoint with the one you created before
- Replace the credentials with the Capella database credentials you created before
- Replace the privatelink-cert.pem with your certificate name.
- Save the file as example.py.
- Copy the following simple python code in your preferred IDE.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
import sys from couchbase.cluster import Cluster from couchbase.options import ClusterOptions from couchbase.auth import PasswordAuthenticator cluster = Cluster('couchbases://o3zak2eyqhmw2tq.pl.cloud.couchbase.com', ClusterOptions(PasswordAuthenticator("privatelinkcapella","Couchbase123$",cert_path="/home/ec2-user/privatelink-cert.pem"))) bucket = cluster.bucket('travel-sample') collection = bucket.scope('inventory').collection('airline') try: result = collection.get('airline_10') print(result.content_as[dict]) except: print("exception:", sys.exc_info()[0]) |
-
- Copy the example.py file into your ec2 instance. Same as previously, replace the certificate with your own, as well as the ec2 name with your own.
|
1 |
scp -i "NishantNVirginia.pem" example.py ec2-user@ec2-18-212-126-71.compute-1.amazonaws.com:/home/ec2-user |
-
- SSH into your EC2 instance again.
-
1ssh -i "NishantNVirginia.pem" ec2-user@ec2-18-212-126-71.compute-1.amazonaws.com
- Check that both your acme-cert.pem and your example.py file are there.
|
1 2 |
[ec2-user@ip-10-0-12-174 ~]$ ls example.py privatelink-cert.pem |
-
- Run your Python script. You should get the JSON document airline_10.
|
1 2 3 |
[ec2-user@ip-10-0-12-174 ~]$ python3 example.py {'id': 10, 'type': 'airline', 'name': '40-Mile Air', 'iata': 'Q5', 'icao': 'MLA', 'callsign': 'MILE-AIR', 'country': 'United States'} |
4. Test curl commands connecting to the Capella Private Endpoint
-
- Still in the EC2 instance, try a SQL++ query using Server REST APIs. Replace the private endpoint with yours.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
[ec2-user@ip-10-0-12-173 ~]$ curl -u privatelinkcapella:Couchbase123$ --data-urlencode "statement=select * from `travel-sample`.inventory.airline limit 1;" https://o3zak3eyqhmw2tq.pl.cloud.couchbase.com:18093/query/service --insecure { "requestID": "9c201945-9252-4a14-806a-6ed948faa3e4", "signature": {"*":"*"}, "results": [ {"airline":{"id":10,"type":"airline","name":"40-Mile Air","iata":"Q5","icao":"MLA","callsign":"MILE-AIR","country":"United States"}} ], "status": "success", "metrics": {"elapsedTime": "7.410508ms","executionTime": "7.367052ms","resultCount": 1,"resultSize": 132,"serviceLoad": 6,"usedMemory": 127}, "profile": {"phaseTimes": {"authorize":"1.134491ms","fetch":"1.662602ms","instantiate":"758.586µs","parse":"321.378µs","plan":"147.303µs","primaryScan":"3.249994ms","project":"2.5µs","run":"6.129593ms","stream":"6.55µs"},"phaseCounts": {"fetch":1,"primaryScan":1},"phaseOperators": {"authorize":1,"fetch":1,"primaryScan":1,"project":1,"stream":1},"requestTime": "2024-01-04T17:48:45.956Z","servicingHost": "svc-dqis-node-002.o3zak2eyqhmw2tq.cloud.couchbase.com:8091","executionTimings": {"#operator":"Authorize","#stats":{"#phaseSwitches":4,"execTime":"3.122µs","servTime":"1.131369ms"},"privileges":{"List":[{"Target":"default:travel-sample.inventory.airline","Priv":7,"Props":0}]},"~child":{"#operator":"Sequence","#stats":{"#phaseSwitches":1,"execTime":"8.805µs"},"~children":[{"#operator":"PrimaryScan3","#stats":{"#itemsOut":1,"#phaseSwitches":7,"execTime":"16.575µs","kernTime":"3.142µs","servTime":"3.233419ms"},"bucket":"travel-sample","index":"def_inventory_airline_primary","index_projection":{"primary_key":true},"keyspace":"airline","limit":"1","namespace":"default","scope":"inventory","using":"gsi"},{"#operator":"Fetch","#stats":{"#itemsIn":1,"#itemsOut":1,"#phaseSwitches":10,"execTime":"17.868µs","kernTime":"3.264724ms","servTime":"1.644734ms","usedMemory":127},"bucket":"travel-sample","keyspace":"airline","namespace":"default","scope":"inventory"},{"#operator":"InitialProject","#stats":{"#itemsIn":1,"#itemsOut":1,"#phaseSwitches":8,"execTime":"132.805µs","kernTime":"4.943451ms","state":"running"},"discard_original":true,"result_terms":[{"expr":"self","star":true}]},{"#operator":"Limit","#stats":{"#itemsIn":1,"#itemsOut":1,"#phaseSwitches":4,"execTime":"2.823µs","kernTime":"1.265µs","usedMemory":127},"expr":"1"},{"#operator":"Stream","#stats":{"#itemsIn":1,"#itemsOut":1,"#phaseSwitches":6,"execTime":"6.55µs","kernTime":"4.956921ms"}}]},"~versions":["7.2.3-N1QL","7.2.3-6705-enterprise"]}}, "controls": {"scan_consistency": "unbounded","use_cbo": "true","n1ql_feat_ctrl": "76","stmtType": "SELECT"} } |
-
- Still in the EC2 instance, try an Analytics query using Server REST APIs.
|
You have now established a private connection between your AWS VPC and Couchbase Capella using a Private Link!
Conclusion
Implementing AWS Private Link for Couchbase Capella is crucial for enhancing the security and reliability of your data communication. By establishing a private connection between your VPC and Couchbase Capella, you effectively isolate traffic from the public internet, reducing the risk of exposure to potential threats. This approach ensures that data remains within your secure network boundaries, utilizing AWS’s robust infrastructure to maintain low latency and high throughput. AWS Private Link provides only uni-directional communication, ensuring that data flows securely from your resources to Couchbase Capella without any reverse path. This makes AWS Private Link a highly secure and efficient solution for enterprise-grade database connectivity.