For decades, “the last mile” has been one of the weakest parts of Internet infrastructure. Today, mobile operators are ready to change that by providing reliable and fast connectivity with LAN-like latency for mobile applications. The introduction of AWS Wavelength allows developers to tap into the modern 5G networks and bring their application infrastructure closer to their clients by deploying it directly at mobile operator data centers.
Wavelength zones is a new technology that we at Couchbase were excited to explore during our preparation for AWS re:Invent 2021. To showcase its possibilities and how our master-less architecture makes edge computing easier, we presented a demo auction application that allows Verizon users in Las Vegas to compare request latencies between the classic us-west-2 AWS region and the Las Vegas Wavelength edge zone. This blog post reviews how you can use the power of Couchbase Sync Gateway to start handling your data at the edge.
Setting up the bastion server
Wavelength instances have IP addresses that are assigned by the mobile operator and accessible only from the carrier’s network and your VPC. This makes it impossible to connect to these instances from outside of the carrier’s network.
Therefore, to administer Wavelength instances, a devops engineer must either be connected to the operator’s network directly or use workarounds like bastion servers, which, in simplest cases, can be just an instance in your AWS VPC that is deployed to a regular availability zone.
Let’s first create an AWS EC2 private key that we will use to access the jump server:
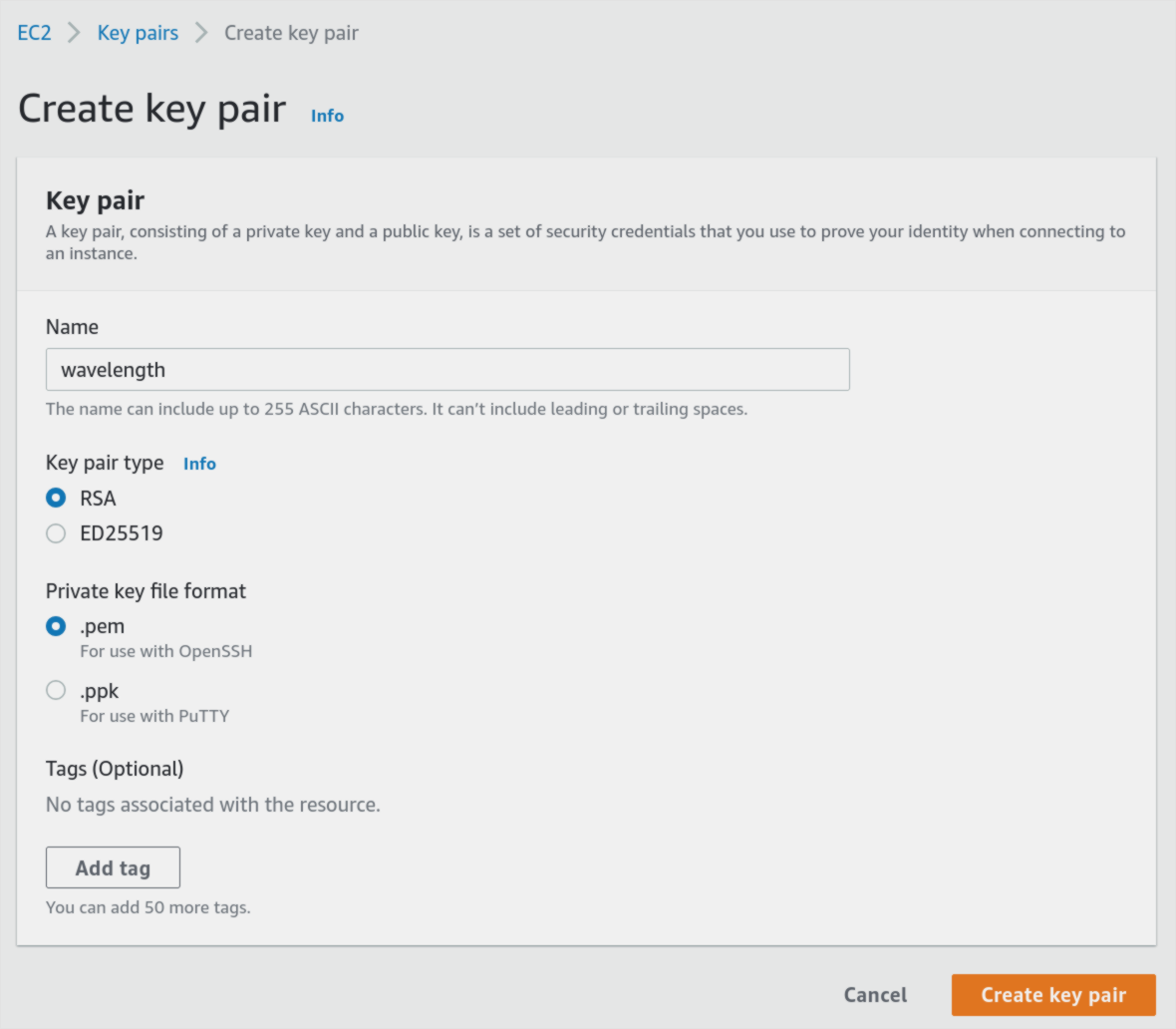
Create the key pair, download it and store it in a secure place. You will not be able to access it later.
Now, we can deploy an Amazon Linux instance that will become our ssh jump host. Don’t forget to assign a public IP address to it, configure its security group to allow inbound and outbound ssh connections, and specify the key pair when starting the instance:
Verify that you can access the bastion node from your computer:
- If you don’t have it already, start an ssh-agent by running: eval $(ssh-agent -s)
- Add the downloaded key to it by running: ssh-add <path to downloaded pem file>
- Connect to the instance: ssh <public ip of the bastion>
To log into instances that we will later create in the Wavelength zone, use the -J argument of ssh command: ssh -J <public ip of the bastion> <internal ip of the instance>.
Setting up the Wavelength zone
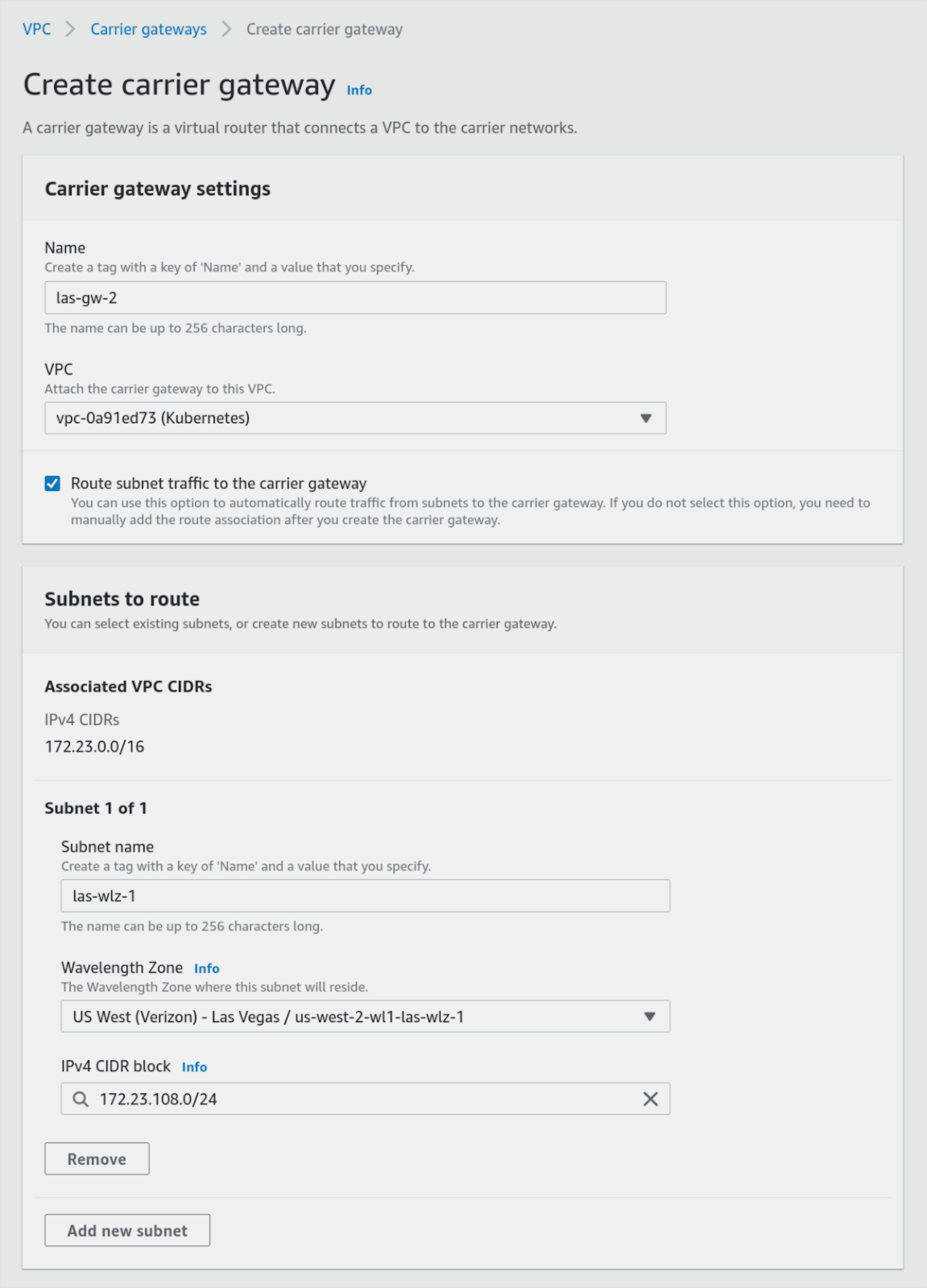
In this example, we will use Las Vegas Verizon (usw2-wl1-las-wlz1) as our edge zone. In order to deploy instances into it and assuming that a VPC in us-west-2 region was created earlier, we need to first create a:
- Carrier gateway to connect our edge instances to both the Internet and operator network
- Subnet that we will deploy our instances onto
- Routing table that directs internet traffic to and from subnet via the carrier gateway
AWS allows us to do all this in a single step when using their Create carrier gateway tool shown below. It also takes care of creating a routing table that will route traffic between instances in the subnet and carrier infrastructure:
Setting up Couchbase Cluster
After the subnet is created, we can proceed to create EC2 instances for our future clusters. There are multiple ways to deploy Couchbase, here are two of them:
The easiest is to create a Kubernetes cluster and use our autonomous operator to deploy and manage the Couchbase cluster. Note that EKS clusters and autoscaling groups require 2 subnets in different regions. Although there are multiple Wavelength availability zones, all these zones are located in different cities. If you want to guarantee that your cluster is located in Las Vegas, you would have to create your cluster manually. Please refer to Couchbase Autonomous Operator documentation for installation instructions.
An alternative way is to install Couchbase directly onto EC2 instances and configure it manually. This is the approach we took for our re:Invent presentation. Instructions on installing Couchbase can be obtained from our documentation.
Note that only a limited set of EC2 instance types are supported by the Wavelength infrastructure. For this presentation, we chose t3.xlarge as Couchbase and Sync Gateway nodes.
It is recommended to use different SSH keys for different servers, or at least different clusters. In order to use the bastion host, you will need to add every SSH key you create to your SSH agent by running: ssh-add <key file>.
Setting up Sync Gateway
The Sync Gateway setup procedure is documented extensively in the Couchbase documentation here. TLS encryption is supported by the gateway out of the box. To configure it, provide paths to the certificate and its private key via SSLCert and SSLKey configuration properties; this will change the ports used by gateway service to SSL ports.Alternatively, a reverse proxy like NGINX can be used to add transport layer security encryption as we did for the presentation. Here is an NGINX configuration you can use to proxy Sync Gateway connections:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 |
server { listen 4984 ssl; server_name example.com; ssl_certificate /etc/letsencrypt/live/example.com/fullchain.pem; ssl_certificate_key /etc/letsencrypt/live/example.com/privkey.pem; client_max_body_size 20m; location / { proxy_set_header Host $host; proxy_set_header X-Forwarded-Host $host; proxy_set_header X-Forwarded-Proto $scheme; proxy_set_header X-Real-Ip $remote_addr; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header Upgrade $http_upgrade; proxy_set_header Connection $connection_upgrade; proxy_pass http://gateway_node:4984; proxy_http_version 1.1; proxy_pass_request_headers on; proxy_pass_header Accept; proxy_pass_header Server; keepalive_requests 1000; keepalive_timeout 360s; proxy_read_timeout 360s; } } |
Although most of this configuration represents a common solution to proxying web sockets, the last three lines configure network timeouts that are more suitable for mobile applications in which stability of the internet connection may suffer at any moment.
Another important instruction is client_max_body_size which raises the limit on how much information mobile devices can send in a single websocket connection.
Conclusion
Couchbase is naturally the database of choice for edge deployments. Out of the box, it provides you with the opportunity to choose from a set of services that any application can benefit from:
- Couchbase Lite, an embedded database that provides easy document synchronization with Couchbase clusters
- Sync Gateway or XDCR replication between different edge or cloud locations
- Robust in-memory and on-disk key-value storage based on widely supported Memcached protocol
- Built-in caching layer
- Full-text search capabilities
- Rich document storage with incredible N1QL language
- Eventing service for reactive programming and data enrichment
- Analytics service that allows extracting insights from your data without affecting the performance of your application
Paired with ultra-low latency of Wavelength edge zones, these features provide a powerful platform for any mobile application and we are excited about solutions that can be built with it.
Resources
To follow up, review some of the links to the resources mentioned in this blog post: